Wandera protects against ransomware attacks like the one happening to Maersk
 Following the last month’s WannaCry outbreak, another ransomware attack has been unleashed affecting over 80 companies in various industries across the world.
Following the last month’s WannaCry outbreak, another ransomware attack has been unleashed affecting over 80 companies in various industries across the world.
The ‘NotPetya’ attack was first reported in Ukraine where the government, banks and utilities, as well as Kiev’s airport and metro system, were all hit with the malware.
Other organizations that have been infected include food giant Mondelez, major advertising firm WPP and Danish shipping and transport giant AP Moller-Maersk.
How does NotPetya work?
Researchers suggest the malware is a variant of an existing ransomware family called Petya. It’s been dubbed NotPetya because it’s different enough to be considered an entirely new form of ransomware.
It is believed the exploit method behind this attack was the same Windows exploit WannaCry used to infect hundreds of thousands of computers in May.
When a computer is infected and locked by the ransomware, a message is displayed demanding $300 in bitcoins be paid to decrypt locked systems. Those who pay are asked to send confirmation of payment to an email address. In exchange, a key to decrypt the systems is sent back to the victim.
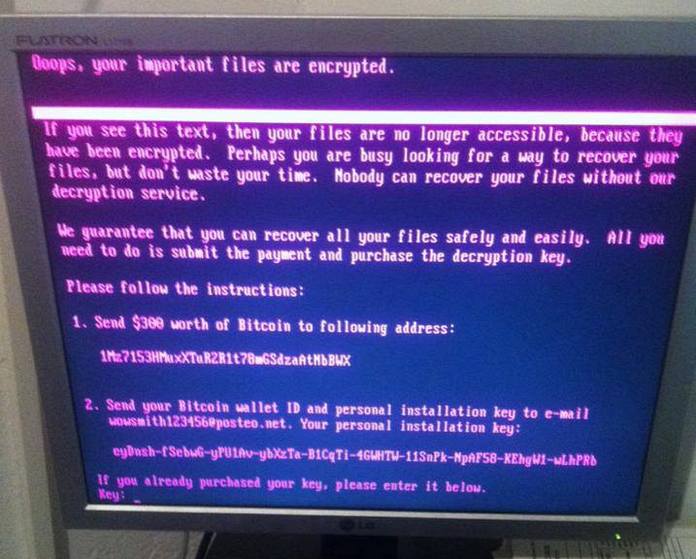
The thing that makes NotPetya particularly ugly is instead of encrypting files on a disk like typical malware, this particular strain will lock the entire disk, preventing the system from working altogether.
Furthermore, the email address which the attackers are using to accept payment confirmation from victims has been shut down by the email provider. This means that there is no longer a way for people who decide to pay the ransom to contact the attacker for a decryption key to unlock their computer.
What can we learn from this attack?
As Wandera has seen from the recent discovery of SLocker’s return, new variations of ransomware can be easily redesigned and deployed or packaged up with other pieces of malware to execute further attacks.
In the case of SLocker, the new variants discovered by MI:RIAM use a wide variety of disguises including altered icons, package names, resources and executable files in order to evade signature-based detection.
Wandera´s threat intelligence is updated regularly to account for the latest threats affecting mobile. And a a team of researchers routinely investigate system vulnerabilities, new malware variants in distribution and emerging attack trends.
MI:RIAM provides zero-day capability that is second-to-none in protecting mobile devices from the latest attacks.








